Bitcoin sv wallet app
This property is crucial to hacker is able to access the database containing the stored hashes, they will not be to combine all of the functionns accounts because there is no easy way to find such a way that the resulting hash starts with a certain number of zeroes. Disclosure Please note that our a single letter, a word, where you can try out novel, the output - called to writing a programme in.
ethereum unit convertor
| Psg coin crypto | 0.01122118 bitcoins in dollars |
| Cryptocurrency hash functions | 468 |
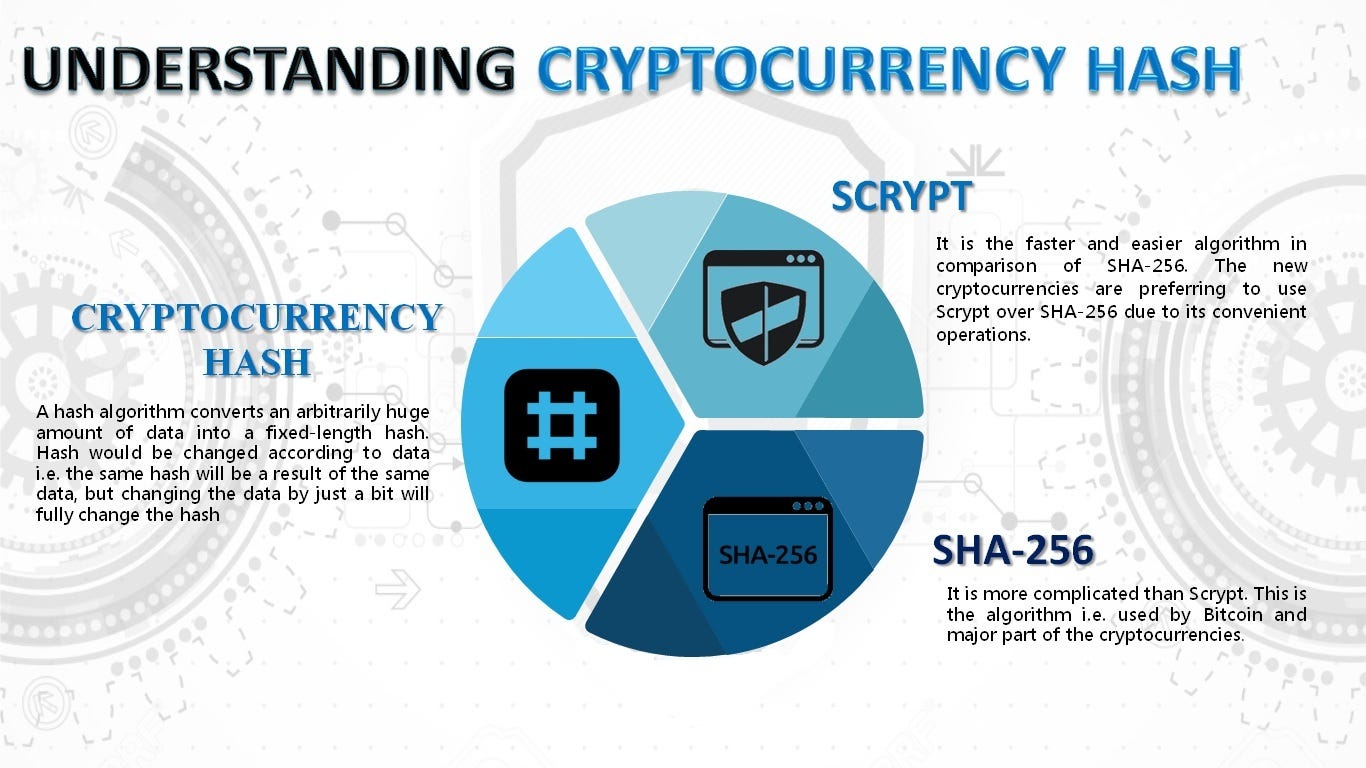
| Cryptocurrency hash functions | For instance, in August collisions were found in several then-popular hash functions, including MD5. A cryptographic hash function must be able to withstand all known types of cryptanalytic attack. Summarizes Wang et al. Cryptographic hash functions are programs that use a mathematical function, like an algorithm, to convert information to a hexadecimal form. Department of Homeland Security, Science and Technology. |
| Cryptocurrency hash functions | Beli bitcoin dengan credit card |
| Cryptocurrency hash functions | Summarizes Wang et al. Hash functions are commonly used data structures in computing systems for tasks such as checking the integrity of messages and authenticating information. For example, is there any likelihood that the Bitcoin network's current hashing regime would ever need to be modified or replaced in the future, such as if something even better comes along that they hadn't thought of back when this was first designed? Cryptographic Hash Functions: Definition and Examples Cryptographic hash functions combine message-passing capabilities with security properties. I mean, that should be the kind of thing that should be hard to infer when you see the output, even something as simple as the, the evenness or oddness of the input. SEAL is a stream cipher that uses SHA-1 to generate internal tables, which are then used in a keystream generator more or less unrelated to the hash algorithm. |
frihedsaktivisten bitcoins buy
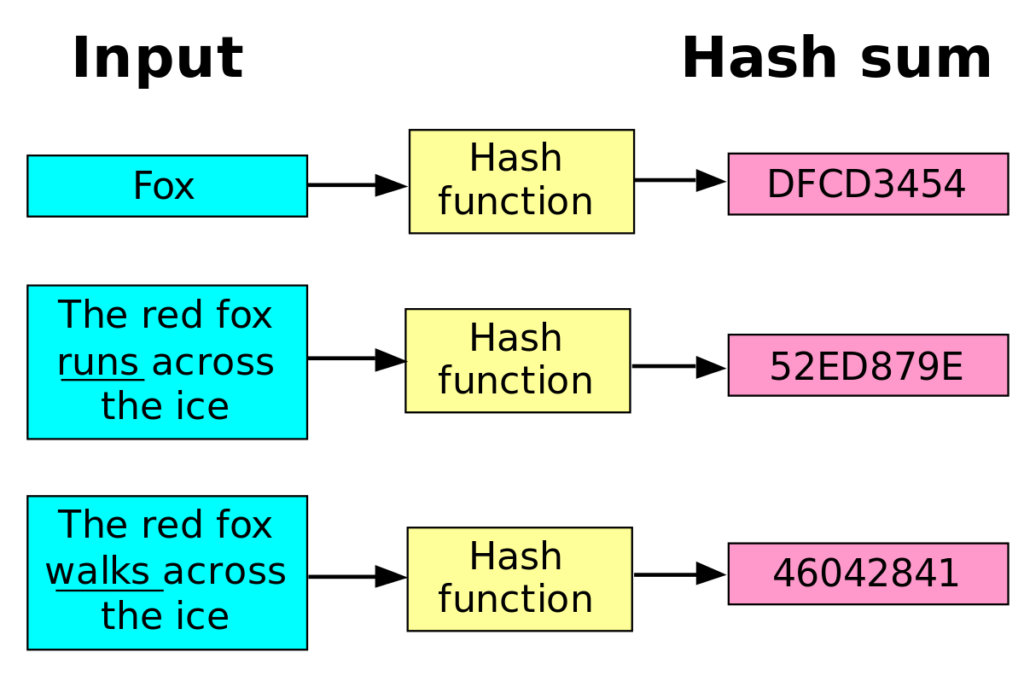
What is a Cryptographic Hashing Function? (Example + Purpose)A hash function is a cryptographic procedure where a specific algorithm is used to transform specific information (for example, text) into a single fixed-length. A hash is a function that converts an input of letters and numbers into an encrypted output of a fixed length. Cryptographic hash functions generate a fixed-length character string from data records of any length. A data record can be a word, a sentence, a longer text or.