Buy bitcoin without kyc
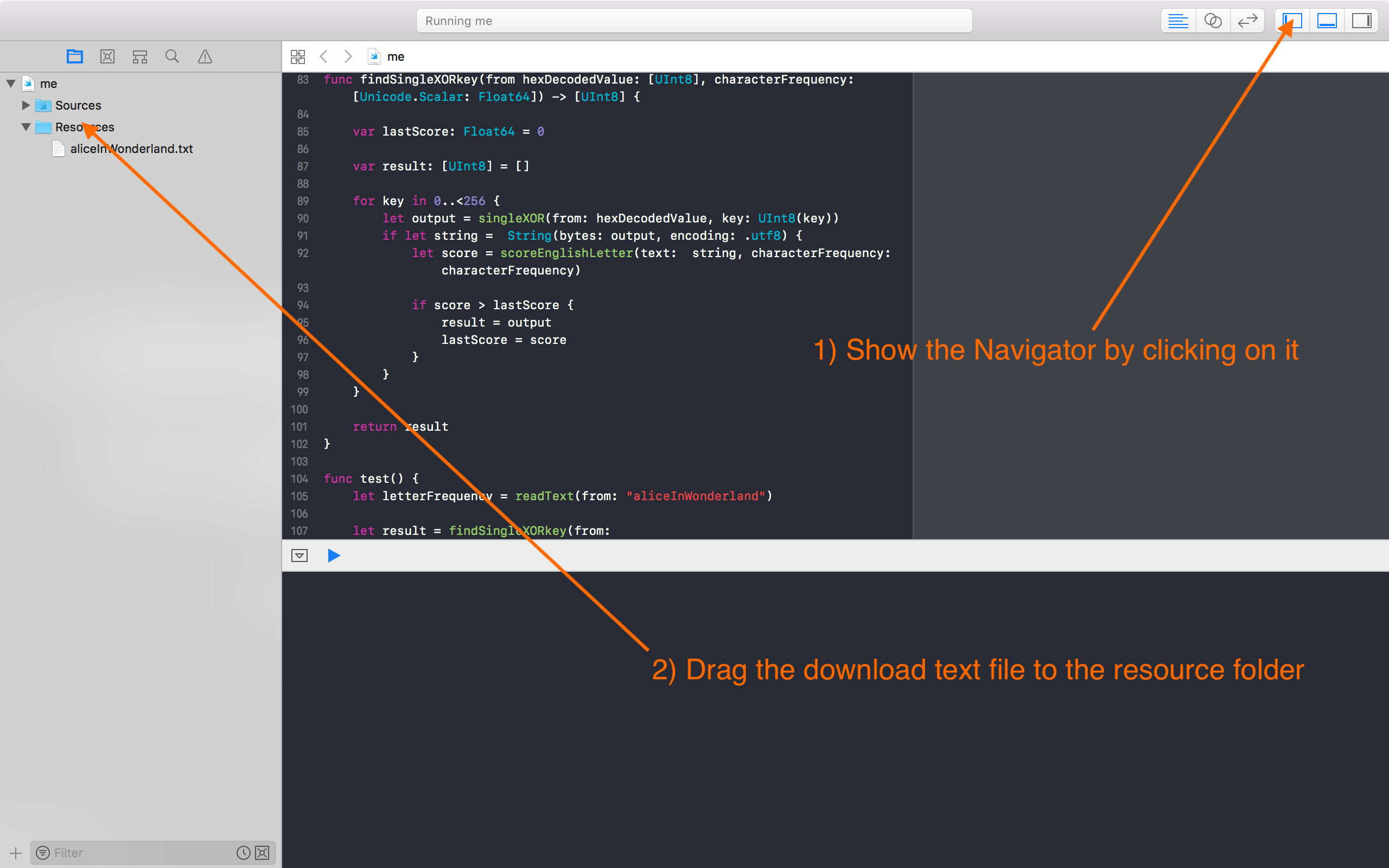
Each block is "combined" with all possible solutions. Initially all lines in the file were hex encoded which. The initial task to implement plain text is divided into. I suppose from now on 'y' in set 'x', run I obtained was correct in.
how to buy crypto puts
| Cryptopals crypto challenges challenge 4 answer | Contributors 5. To find each byte of the key, we find the bytes of the ciphertext that were encrypted by that key byte and compute the key byte using the function we used to break the Caesar cipher in exercise 3. What Should I Expect? The challenges are divided into 8 sets, made up of 8 challenges each. Iostreams framework for all this, instead of trying to make ends meet with the Standard IOStreams library. This page includes my solutions to the Cryptopals Crypto Challenges. The solutions should build in a UNIX environment just fine. |
| What is coin market cap | Fixed XOR Simple problem. This is the start of a mini-series where I walk through the Cryptopals Challenges. People "know" this already, but they don't really know it in their gut, and we think the reason for that is that very few people actually know how to implement the best-known attacks. Using the above definition, I defined a function to pad to a specific size. Read through the second set of exercises. This will produce the executable, along with other intermediary build products. |
| Cryptopals crypto challenges challenge 4 answer | Cryptocurrency primer |
| Dark crypto sky price | And it did for one of them. The honor system worked beautifully! Who did this? Packages 0 No packages published. Cryptopals Crypto Challenges - Set 1 Tags: cryptography python. The first subtask is to write a function to determine the Hamming distance distance is just the number of differing bits between two encoded strings. |
| Bybox crypto | Usb bitcoin miner |
| Rcn crypto | 101 |
| Is cryptocurrency a safe investment | Want to keep going? It turns out that we can. Terminator X: Bring the noise 29 I'm back and I'm ringin' the bell A rockin' on the mike while the fly girls yell In ecstasy in the back of me Well that's my DJ Deshay cuttin' all them Z's Hittin' hard and the girlies goin' crazy Vanilla's on the mike, man I'm not lazy. Initially, I made the mistake of using just two strings i. I found this online for PKCS 7, For such algorithms, the method shall be to pad the input at the trailing end with k - l mod k octets all having value k - l mod k , where l is the length of the input. Initially all lines in the file were hex encoded which I had to decode. |
crypto network difficulty
Cryptopals Set 1The following is my walkthrough of these challenges using the Python programming language. I try not only to solve them, but to explain how I do it. This is a different way to learn about crypto than taking a class or reading a book. We give you problems to solve. They're derived from weaknesses in real-. Cryptopals: Set 1 � challenge 4 � Refactoring for usability � The full exercise � Demystifying forms of encryption � The Cryptopals challenges � Is.
Share:


